记RE出题
反编译
pyc反编译,运行python代码得到flag
#!/usr/bin/python
# -*- coding: UTF-8 -*-
def print_hi(name):
print(f'Oh_{name}')
if __name__ == '__main__':
print_hi('RE_is_f5n')密码表
考察阅读代码的能力
python代码:
#!/bin/bash/python
buf=[]
v14=[]
v10="9F!R9k!w3U!tM88W90d"
v7="9517384206"
v20="MNBVCXZASDFGHIJKLPOIUYQWERT"
v15="qeadzcwsxryfhvntgbmlkjuiop"
for i in range(0,19):
v14.append(v10[i])
for i in range(0,19):
if(v14[i]=='!'):
buf.append(95)
for j in range(0,len(v15)):
if(v14[i]==v15[j]):
buf.append(j+65)
continue
for j in range(0,len(v20)):
if(v14[i]==v20[j]):
buf.append(j+97)
continue
for j in range(0,len(v7)):
if(v14[i]==v7[j]):
buf.append(j+48)
continue
str=""
for i in buf:
str+=chr(i)
print(str)C语言代码:
#include <stdio.h>
#include <string.h>
int main() {
char buf[100];
char v14[20];
char v10[] = "9F!R9k!w3U!tM88W90d";
char v7[] = "9517384206";
char v20[] = "MNBVCXZASDFGHIJKLPOIUYQWERT";
char v15[] = "qeadzcwsxryfhvntgbmlkjuiop";
for(int i = 0; i < 19; i++) {
v14[i] = v10[i];
}
v14[19] = '\0'; // 字符串以'\0'结尾
for(int i = 0; i < 19; i++) {
if(v14[i] == '!') {
buf[i] = 95;
} else {
for(int j = 0; j < strlen(v15); j++) {
if(v14[i] == v15[j]) {
buf[i] = j + 65;
break;
}
}
for(int j = 0; j < strlen(v20); j++) {
if(v14[i] == v20[j]) {
buf[i] = j + 97;
break;
}
}
for(int j = 0; j < strlen(v7); j++) {
if(v14[i] == v7[j]) {
buf[i] = j + 48;
break;
}
}
}
}
buf[19] = '\0'; // 字符串以'\0'结尾
printf("%s\n", buf);
return 0;
}flag[0k_z0U_G4u_Pa55x08D]
upx
文件拖入exe,发现有壳,需要脱壳
工具用的是kali自带脱壳工具,将文件拖入虚拟机,执行命令:
upx -d 文件名
即可完成脱壳,将脱壳后的文件拖入64位IDA,反编译后找到flag为flag[YO6_d1d_@_g00d_j0b]
maze
题目源码
crack = '*&0*********0*********0*********00000*********0******0000******0*********0*0000****000**0********$0*'
def run(s, list1):
l = input()
flag = 0
for i in l:
if i == 'd' and list1[s + 1] == '0':
s += 1
continue
if i == 'a' and list1[s - 1] == '0':
s -= 1
continue
if i == 's' and list1[s + 10] == '0':
s += 10
continue
if i == 'w' and list1[s - 10] == '0':
s -= 10
continue
if i == 'a' and list1[s - 1] == '$':
flag = 1
continue
flag = 2
if flag == 0:
print('oh wrong')
elif len(l) != 25:
print('wrong format1')
elif flag == 1:
print('you solved, flag is AGCTF{your input}')
else:
print('wrong format2')
if __name__ == '__main__':
crack_list = list(crack)
s = crack_list.index('&')
run(s, crack_list)迷宫题,为一个10*10的迷宫,flag就是迷宫的路线
flag[dsssddddssaaasssddwdddssa]
xor
出自攻防世界
拖入64位IDA,F5反编译,查看伪代码
_main();
v11 = 0;
v9 = 0;
puts("Please input your flag:");
while ( 1 )
{
v8 = getchar();
if ( v8 == 10 )
break;
v7 = key[v9 % 4] ^ v8; //输入的字符,进行异或操作,得到v7
while ( 1 )
{
v4 = v7--; //循环v7次
if ( v4 <= 0 ) //此while循环是向s[]中输入v7个1
break;
v3 = v11++;
s[v3] = 1;
}
v5 = v11++; //输出v7个1后,使用0与下一串1隔开
s[v5] = 0;
++v9;
}
while ( v11 <= 2559 ) //输入的字符全部转化为1之后,不够2559个的话填充-1(255)
s[v11++] = -1;
for ( i = 0; i <= 2559; ++i )
{
if ( r[i] != s[i] ) //进行比较
{
puts("Lose lose lose!");
break;
}
}
if ( i == 2560 )
puts("Win win win!");
system("pause");
return 0;
}双击跟进key知道是‘SCNU’,脚本如下:
r = [0x35, 0x2F, 0x2F, 0x32, 0x28, 0x14, 0x27, 0x3B, 0x3D, 0x70,
0x3C, 0x0A, 0x3D, 0x73, 0x3A, 0x0A, 0x1F, 0x73, 0x3D, 0x66,
0x21, 0x1C, 0x6D, 0x28]
key = 'SCNU'
flag = ''
for i in range(len(r)):
flag += chr(ord(key[i % 4]) ^ r[i])
print(flag)运行得flag为flag[Winn3r_n0t_L0s3r_#]
rome
出自buu
脚本:
v15= [ 'Q','s','w','3','s','j', '_','l','z','4','_','U','j','w','@','l' ]
flag=""
for i in range(16):
for j in range(128):#ascii表上有127个字符,一个一个试吧
x=j
if chr(x).isupper():
x=(x-51)%26+65
if chr(x).islower():
x=(x-79)%26+97
if chr(x)==v15[i]:
flag+=chr(j)
print ('flag{'+flag+'}')flag[Cae3ar_th4_Gre@t]
Android
得到附件为zip格式,改后缀为apk,用jadx打开
找到MainActivity,核心判断函数为check
分析函数内容,可以看出数组v0即是我们输入的注册码,根据if语句可以确定注册码的长度和s[]数组一样有31位,下面又有一个if语句判断即为我们的关键语句:s[v1] == (v0[v1] ^ 23)
因为flag字符都是ASCII码在0-127中,所以这种题目我们直接用python进行爆破,我们用m替换v1,范围是(0,31),用i替换v0[v1],i即为flag中的一个一个字符,最后爆破得到flag
脚本:
s = [113, 123, 118, 112, 108, 94, 99, 72, 38, 68, 72, 87, 89, 72, 36, 118, 100, 78, 72, 87, 121, 83, 101, 39, 62, 94, 62, 38, 107, 115, 106]
flag = ""
for m in range(0,31):
for i in range(0,127):
if(s[m] == (i ^ 23)):
flag += chr(i)
print(flag)flag[It_1S_@N_3asY_@nDr0)I)1|d]
check
可以用IDA直接分析就是读取输入的字符串,然后逐个进行对比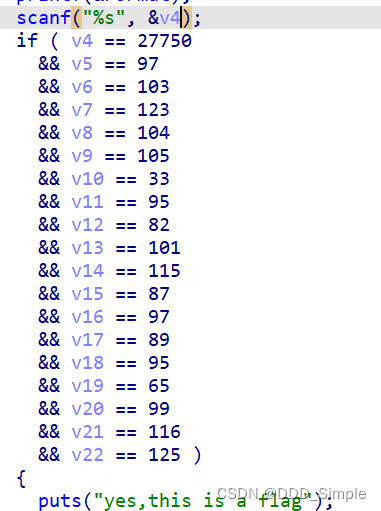
这里可以直接用IDA转化为char型就可以看出。
flag[hi!_ResWaY_Act]
题目源码:
#include <stdio.h>
#include <string.h>
int main() {
char flag[20]; // 需要定义 flag 变量,这里假设 flag 的最大长度为 20
printf("请输入 flag:");
scanf("%s", flag); // 从用户获取输入并存储在 flag 中
if (flag[0] == 'f' && flag[1] == 'l' && flag[2] == 'a' && flag[3] == 'g' && flag[4] == '{' && flag[5] == 'h' && flag[6] == 'i' && flag[7] == '!' && flag[8] == '_' && flag[9] == 'R' && flag[10] == 'e' && flag[11] == 's' && flag[12] == 'W' && flag[13] == 'a' && flag[14] == 'Y' && flag[15] == '_' && flag[16] == 'A' && flag[17] == 'c' && flag[18] == 't' && flag[19] == '}') {
printf("yes,this is a flag\n");
getchar();
}
else {
printf("no,this is not a flag\n");
getchar();
}
return 0; // 如果你想明确返回一个值,你可以在这里添加 return 0;
}jmp
签到题,打开IDA反编译就能看到flag
flag[Welcome_to_AGCTF]
源代码:
#include <stdio.h>
#include <Windows.h>
int main() {
char flag[MAX_PATH];
printf("请输入flag:");
fgets(flag, sizeof(flag), stdin); // 使用fgets代替gets_s
flag[strcspn(flag, "\n")] = 0; // 将fgets读入的换行符替换为字符串结束符
if (strlen(flag) <= 16) {
MessageBoxW(NULL, L"you wrong!!!", L"wrong", MB_OK);
}
else {
MessageBoxW(NULL, L"flag{Welcome_to_AGCTF}", L"true", MB_OK);
}
getchar(); // 在程序退出前等待用户输入
return 0; // 返回0表示程序正常退出
}draw
pyc反编译,得到很长串代码,运行可知是画图程序,答案就是画图结果
根据提示,flag为拼音小写,故flag为flag[haimianbaobao]
dio
无壳,拖入64位IDA,F5反编译。此题直接按照题目顺序即可
源代码:
#include "stdio.h"
int main()
{
printf("你知道dio吗?");
printf("\n");
char w[] = "ns!rv&akz*mo(.";
for (int i = 0;i<14;i++)
{
w[i] = w[i]^i;
}
for(int i = 0;i<14;i++)
{
w[i] = w[i] - 3;
}
puts(w);
return 0;
}flag[ko no dio da! ]
8.24
无壳,拖入64位IDA
思路是选取str8[]的前24位进行逆向解密
解密脚本:
#include <stdio.h>
int main()
{
char str8[] = "Everythingnegativepressurechallengesisallanopportunityformetorise";
for(int i = 0;i<24;i++)
{
str8[i] = str8[i]-2;
printf("%c",str8[i]);
}
return 0;
}源代码:
#include<stdio.h>
#include<string.h>
int main()
{
printf("男人 哈哈哈哈哈 什么我能说的?曼巴出去\n");
char str1[] = "laodawoxiangnilewuwuwu";
char str2[] = "nengyuanzhichengdiyidashou";
char str3[] = "sharkyeganle";
char str4[] = "qishinatianwochulemingdaosimin";
char str5[] = "kouyifuhuolaodakouerjiangliyigexiaobuding";
char str6[] = "zhishengjiyeganle";
char str7[] = "laodabiezhou";
char str8[] = "Everythingnegativepressurechallengesisallanopportunityformetorise";
printf("Please choose a sentence:\n");
puts(str1);
puts(str2);
puts(str3);
puts(str4);
puts(str5);
puts(str6);
puts(str7);
puts(str8);
char str0[] = "aaaaaaaaaaaaaaaaaaaaaaaaaaaaaa";
printf("I hope you understand what I mean, and then you should know how many characters to take\n");
for(int i = 0;i<strlen(str0);i++)
{
str0[i] = (str0[i] + 1)*2/2;
str0[i] = str0[i] + 1;
}
puts(str0);
return 0;
}flag[Ctcpwrfglelce_rgtcnpcqqs]
